License Locking Terminology
Before you learn more about locking licenses, it is important to understand the related terminology.
>Client-locked, Server-locked, Client-server Locked, and Unlocked Licenses
>Local License Request Locking Criteria
>Primary and Secondary Locking Criteria
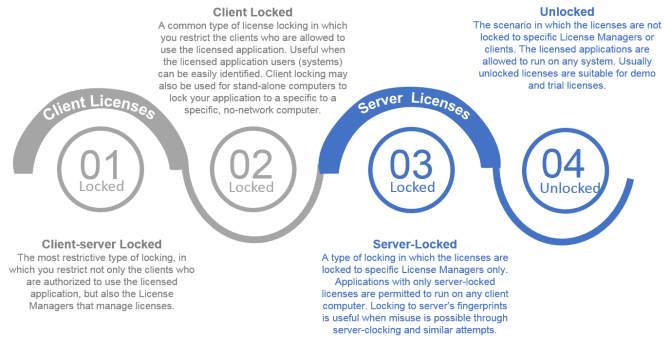
Client-locked, Server-locked, Client-server Locked, and Unlocked Licenses
Sentinel RMS allows locking the licenses to:
>Specific clients - known as client-locked licenses.
>Specific License Managers - known as server-locked licenses.
>Specific clients as well as License Managers - known as client-server-locked licenses.
>None - known as unlocked licenses.
In the diagram below, the various types of locking are displayed:
NOTE A license can be locked to the maximum of seven (7) clients.
Lock Selector
The characteristics of a computer that can be used for fingerprinting a computer. These can be the standard system characteristics (such as the host name or IP address) or hardware-based characteristics (such as the Computer ID Key) or any custom criteria of your choice (such as the display card).
Locking Criteria
One or more lock selectors form a locking criteria. For example,
>Lock selector 1 = IP address
>Lock selector 2 = host name
>Lock selector 3 = Ethernet address
>The locking criteria = 1, 2, or 3 individually, or in combination.
Fingerprint
The value for the locking criterion. The fingerprint distinguishes one computer from another.
Locking Code
A 16-byte long readable string that identifies a computer. However, this string is actually a 64-bit hash value based on SHA-256 algorithm.
See the screenshot below of the Wechoid utility (a Windows-based graphical utility) for better understanding of these terms.
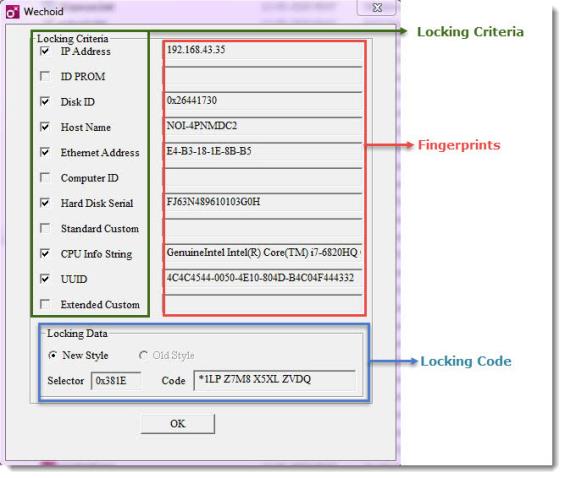
Illustrating Few of the Locking Terms Using Wechoid
Local License Request Locking Criteria
The locking criteria that are useful when network licenses are used on standalone systems as repository, commuter, and grace licenses. For example, the local locking criteria are used for checking out an authorization for a remote commuter license. Thus, the checked out authorization can only be used on the system that meet the local locking criteria requirements.
Local locking criteria can be specified even when the parent network license is unlocked as they will allow further use on qualified local systems only.
NOTE If the local locking criteria is not defined, then disk ID will be used for locking these types of licenses. However, disk ID may be duplicated in certain scenarios (when hard drives are cloned) leading to the SNTL_CLIENT_ALREADY_EXIST error. The disk ID is unavailable for Android devices as they do not support standard fingerprints. To combat these scenarios, the software vendor needs to use CustomEx. When using CustomEx for local license locking, ensure to register the custom locking callback in your application (refer to the procedure for C, Java, and .NET).
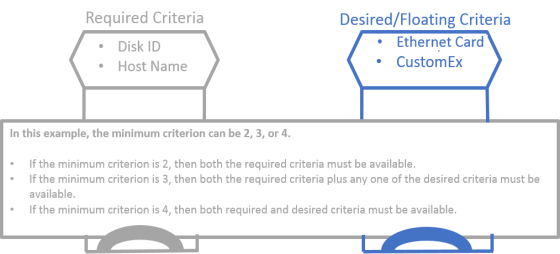
The local license request locking criteria has three parts that you can tailor for flexibly making the licenses available locally (on a client system):
>Required: The necessary locking criteria that must be met by the client system. The disk ID and host name are the required locking criteria in the screenshot below.
>Desired/Floating: The desired locking criteria that should be met by the client system. Ethernet address and CustomEx are the desired locking criteria in the screenshot below.
>Minimum required: The minimum number of locking criteria that must be met by the client system to use the commuter/repository/grace license token locally. This number can be greater than or equal to the number of required criteria and less than or equal to total number of criteria.
Primary and Secondary Locking Criteria
For server-locked licenses, you can specify two sets of locking criteria known as primary and secondary locking criteria. The licensed application will run if any of the locking criteria is matched on the License Manager machine.
NOTE A typical use of primary and secondary locking criteria is to allow fallback for change in the system fingerprint. For example, for a License Manager the Ethernet address can be the primary criteria and the Computer ID Key can be the secondary locking criteria. For high-availability, you can specify primary locking criteria of License Manager 1 and secondary locking criteria of License Manager 2. However, you should do this with caution as it will allow your customers to duplicate the same license on two License Manager hosts. Since the two systems will not be coordinating with each other regarding the number of tokens issued, the number of license tokens available will be actually doubled.
The table below gives some suggested settings for primary and secondary fingerprints:
| Suggestion | Windows | UNIX | Linux ARM | |||
|---|---|---|---|---|---|---|
| Security Option | Group 1 | Group 2 | Group 1 | Group 2 | Group 1 | Group 2 |
| Computer ID key | Disk ID | Computer ID key | ID PROM | Disk ID | ID PROM | |
| Standalone and Network Option | Disk ID | IP address and Ethernet address | ID PROM | ID PROM | ID PROM | ID PROM |
| Laptop Option | Disk ID | IP address and Ethernet address | ID PROM | ID PROM | ID PROM | ID PROM |
| Backup Option | Disk ID | Host Name | ID PROM | Host Name | ID PROM | Host Name |
